For over 15 years, we at ServiTecno have been dealing with Industrial Security, today called OT/ICS Cyber Security, we have seen many control and automation systems and many factory networks, grown over time and without any concern for the Security part, And we have discovered a lot of vulnerabilities sometimes even "layered" under network architectures, operating systems, remote connections and custom and off-the-shelf applications.
What have we learned in recent years about vulnerability assessments of OT/ICS technologies?
We must make a brief introduction: we have been dealing with industrial software for over 40 years, our experience is that of automation engineers.
We therefore mainly evaluate the exposure and risks of the controlled process based on the IT security (and Safety) vulnerabilities inherent in the ICS/OT environment.
But what is an OT/ICS vulnerability assessment?
OT/ICS vulnerability assessment is the process by which an organization identifies potential security gaps due to its software, configuration, network design and architecture, configuration and management of accounts and associated privileges for use and maintenance of the systems, the quality and solidity of the components used: once this information (and many others) is collected, a score is assigned and therefore a priority to identify which of these risks represents the greatest threat to the plant.
In computer security, a vulnerability is defined as a weakness that can be exploited by a malicious actor (hacker?) or accident, then infiltrate and cause damage.
Do you want to monitor your network and discover every single anomaly?
Uses Anomaly Detection for Plants!
Learn more
What are the key steps or components of OT/ICS vulnerability assessment tool:
- A complete inventory of all system/network components including: hardware, software, network configurations, device settings, account and user information, etc.
- Identification of known vulnerabilities based on public databases such as NIST National Vulnerability Database, ICS-CERT, Enisa, etc.
- Assignment of a risk score based on the criticality of the asset, the potential exploit and the impact and, most importantly, the potential impact on the plant/process or with regard to Safety or the protection of people, the environment, the plant itself.
- Prioritize, based on the score above, the “remediation” to mitigate the greatest risks based on the time (and cost) scale

Why is an OT/ICS vulnerability assessment so important?
Because it provides the fundamental data to allow the creation of a solid remediation path for the protection of the systems that manage the plants. Without a correct assessment, there would be the risk of adopting more expensive and low-impact solutions.
With a reliable assessment, everyone involved (and management in particular) will have more confidence that these initiatives to improve security (and of course the associated investments) will give the greatest ROI possible (although often talking about ROI for security is an oxymoron).
Of course, it helps to provide an accurate view of the potential risks that the process could cause in terms of physical damage to people or to the reputation of the Company involved, without considering the legal implications associated with an incident.
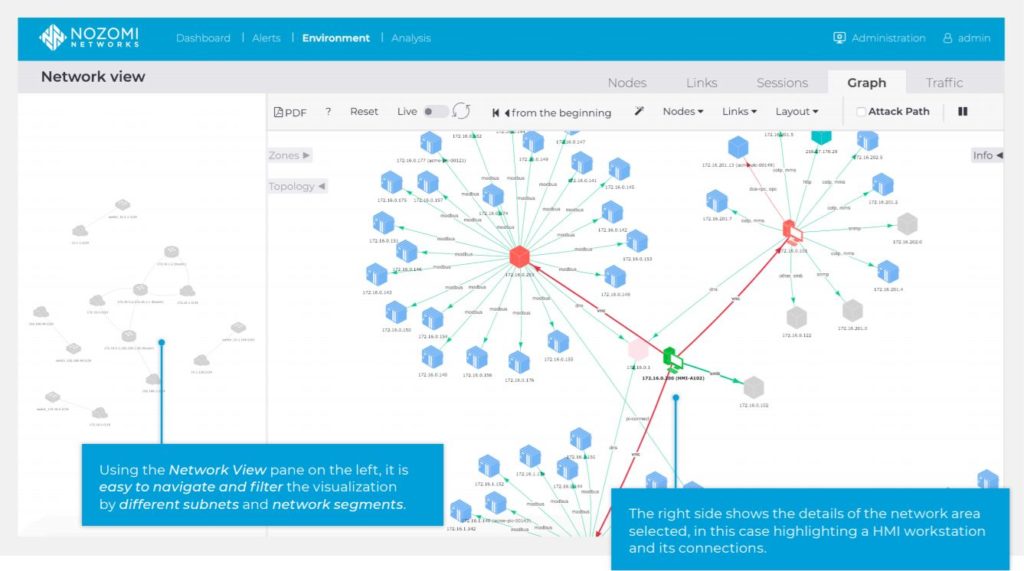
Some findings for "making safety"
Here are some of the most common things that we have identified in these years of experience in the "secure" of industrial networks:
- We use technology to collect a very thorough inventory of everything connected to the factory network: we will need more than just hardware and operating system identification, a detailed patch situation, firmware versions, user and account information, inventory complete with software, etc. all to have one 360° view of what is installed and how it is used. Manual (or sample) inventories have two defects: firstly, they are obsolete in the instant after they are made, and furthermore the vulnerability assessment is only useful if you start the remediation as an obsolete database (even just a few weeks before ) of vulnerabilities is no longer useful in the remediation phase. So, since the tools are there, it's better to use an automated collection to get a 360-degree picture of the risk. Without forgetting that the technology allows not only a much lower cost, but also a more in-depth view of updated vulnerabilities and therefore of the risks.
- Precisely with reference to the above, there are different ways to apply the tsoftware technology to acquire updated information without relying only on IT scanning technologies that put OT devices and processes at risk: those specific to the OT/ICS world suggested, selected and used by us, act only in a "passive" and totally non-intrusive way, therefore without inducing additional risks in the plant's operation, helping to streamline this assessment process.
- The criticality of the OT asset or the impact on the plant/process is as important, if not more, than the exposure of the asset itself. This is one of the most significant differences between IT and OT. Of course, in IT there are some resources (Servers, switches, firewalls, etc.) that are more important. But in OT, some malfunctioning devices can cause an immediate shutdown of a plant, causing damages for tens and hundreds of thousands of euros or, even worse, physical damage to people, the environment or the plant itself.
- In IT, most networked devices can be patched relatively quickly to remediate known or emerging vulnerabilities. Patch management in the OT world can be very slow and sometimes even not possible with the plant running (often you have to wait for the first plant shutdown, sometimes even for months!): we therefore see that the priority of risks and of the most critical devices and to be protected becomes even more important.
- Remediations, even if they arrive on input from the Corporate IT function, often require a "Think Global: Act Local" approach. “Think Global” means that the technology and solution you decide to use should aggregate all site-level risk information into an enterprise-wide view. "Act Local" means that remediation actions are placed in the hands of local personnel who truly understand them and decide the processes, timing and methods of execution. We have seen many horror stories of patches on production PCs, changes in plant network configurations or operator account management, decided by Headquarters IT, which then cause operational problems and downtime in the remote factory connected to Headquarters.
- A proper OT/ICS vulnerability assessment requires a 360° view of risks. In ICS/OT systems, relying on CVE vulnerabilities and published CVSS scores is not enough. We don't want to talk here about the specific OT vulnerabilities (which can be found on ICS-CERT.CISA etc). as the risks in OT/ICS go far beyond the “vulnerabilities” as known to IT. Let's face it: these OT/ICS systems are often "insecure-by-design", as when they were designed, developed and installed, nobody thought about Cyber Security.
This is just a short list of some of our experiences in researching and identifying vulnerabilities in OT/ICS networks and systems.
The tools for their identification, as we have seen, exist and are very effective. Sometimes it is necessary to use specific tools for each type of investigation, as networks and systems can be very different from each other, even if developed for very similar functions and purposes.
As mentioned, network monitoring with continuous identification of vulnerabilities is not only possible, but recommended. Advice from Automation and Industrial Control experts can be very useful here.
This approach can lead to a guided remediation with a view to continuous improvement of the Security (and Safety) of the network and OT/ICS systems.
Do you want to meet an OT Cyber security expert?
Contact us! Our expert will give you all the information, advice and help you need!
Write us




