From the shutdown of the production chain to the theft of sensitive health data, up to the tampering of primary public services, one thing is certain: the continuous evolution of digital threats increasingly involves OT systems, with devastating impacts both in terms of production interruption and of financial losses and potential large-scale consequences, which can go beyond the strictly technological sphere to affect a potentially wider audience, whether they are users of a service or ordinary citizens.
Standardization of ICS connectivity using TCP/IP protocols, convergence between IT, IoT and OT, adoption of 5G, building blocks of the current industry 4.0 which are leading to significant cost reductions and clear improvements in process accuracy and safety, but which at the same time they also bring with them a dark side in the form of IT vulnerabilities amplified precisely by the connectivity of the systems.
In fact, for the past two years, digital adoption has increased at an unprecedented rate and pharmaceutical companies have also rapidly moved towards remote working and cloud-based systems. As also confirmed by the data collected in Iconsulting's "Digital Transformation Barometer", the pharmaceutical sector has increased the budget invested in digital initiatives by 168% compared to 2020.
These innovations and new technologies have led to the creation of hybrid and multicloud environments and to a greater convergence and interdependence between IT and OT. While offering undoubted benefits in automating and optimizing manufacturing environments, industrial IoT (IIoT) technologies open up new security problems and also force legacy operating technology (OT) devices and systems in pharmaceutical manufacturing to converge with IT networks, leaving them exposed to a broader spectrum of threats deriving from IT/OT convergence.
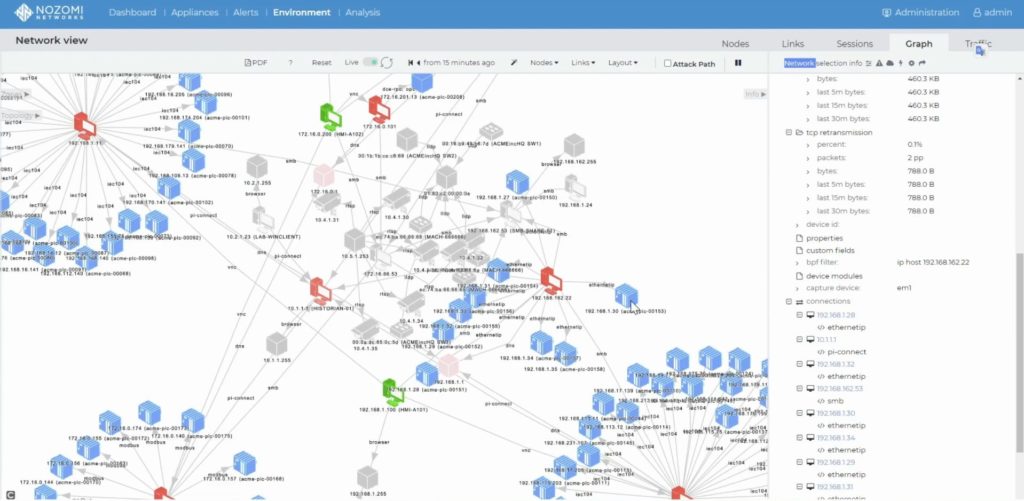
An effective OT security plan must provide for an in-depth and complete verification of the network topology to be protected, in order to highlight any structural vulnerabilities and blind spots and ascertain the quantity and type of connections to and from the outside, and understand the extension of the surface exposed to possible attacks. From these elements, specific tests can be developed to detect the most dangerous vulnerabilities and then define the most adequate protection measures.
To guarantee the protection of the entire supply chain, an approach that includes all aspects of activity management, from administrative ones to production line control, is needed to define an IT / OT security strategy that allows to identify and protect all components that could be a risk factor. Pharmaceutical companies generate and own billions of dollars worth of data, which includes intellectual property, information related to pharmaceutical technology research and development, as well as patient and clinical trial data. In addition, the growing adoption of technologies and solutions offered by third-party suppliers, of IoT devices and activities in the medical field, mainly linked to the study and development of anti-Covid vaccines, have rapidly transformed them into even more attractive targets in the eyes of cybercriminals, increasing the level of risk.

In fact, in the pharma sector "the data equals the product" and companies cannot send a batch of product to hospitals and pharmacies if all the data collected during the production phase have not been associated. This intensifies the need to protect not only production and packaging systems, but also infrastructure, storage, connected databases where information is collected and stored. So, in addition to protecting servers and endpoints, it is vital to ensure the integrity and availability of machines, production lines, networks and connections. Today, in fact, a cyber attack – which in the past would have often been considered as a simple IT problem – is capable of having serious and serious repercussions on production continuity, as recently witnessed by numerous news stories.
OT Security also provides for a protection based on analysis and continuous monitoring of the systems, since it is essential to quickly detect anomalies that can be caused by malfunctions, as well as by attacks.
To allow the company's IT department to respond quickly to a possible cyber attack, it is therefore essential to have extensive visibility on all machines and devices on the network, combined with constant monitoring that allows you to identify unexpected behavior. Frequently, hackers often remain undercover for long periods of time, initially limited to gathering far-reaching information about the infrastructure they have infiltrated. During this latency period, they spread across the entire network and obtain all the necessary access rights to be able to close the trap and launch the actual attack. At this moment they become visible in all respects and can be intercepted by common security systems. But by then it may already be late, critical data may already have been stolen and encrypted, and control over all networked equipment in the hands of hackers.
Once again confirming the old adage "prevention is better than cure", only a preventive protection strategy based on the analysis and correlation of data from multiple areas, in particular OT and IT, allows to achieve sufficient visibility to face the threats before they become critical, in some cases before they even manifest themselves.
