Bayshore is the last line of defense: just like the armored door separates the cockpit from the rest of the aircraft, Bayshore puts your supervisory and control systems, machines and production plants under protection
The digitization processes of the production realities require a pervasive integration of the various information systems present at all levels of the company to allow management full awareness and therefore prompt reactivity that would otherwise be impossible.
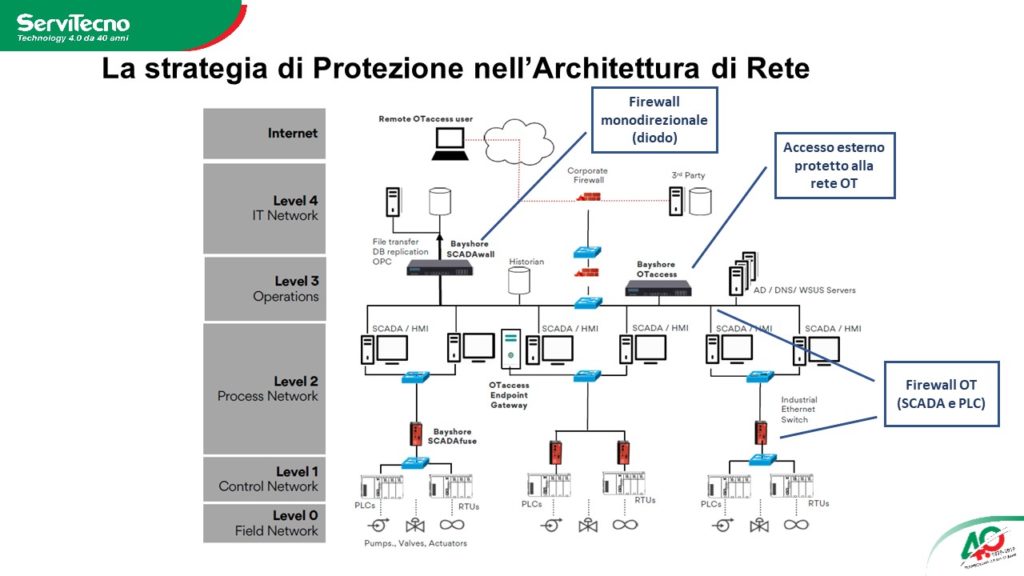
The factory network, to which all production control and automation systems pertain, it is the heart of the production process and contains all those tools that allow you to manage the lines or machines on the plant in real time but at the same time to check their status, to check the actual level of stocks, the quality of the product, etc.
It is clear that the OT network is essential for digitization but also contains critical issues because every IT incident, coming from outside or from other levels of the network, can cause costly and potentially dangerous service interruptions.
According to what is contained in the standard IEC62443, the main guideline in this sector, and as recommended by leading experts, to avoid any propagation of problems and contamination from one area of the network to another, it is necessary to segment the networks as much as possible and in particular the factory network.
Ma the factory network has specific characteristics sometimes very far from the usual IT standards, here are some examples:
- The plants and the electro-instrumental equipment of industrial machinery are often found inside cabinets electrical systems in fixed positions, sometimes distant from each other, probably difficult to reach, certainly cannot be moved.
- The real segmentation of the network, the physical one, is therefore even more complex than you think, and often it turns out difficult to zone all those physically distant and separate endpoints.
- I electrical cabinets are in most cases not air-conditioned it is therefore necessary to install industrial devices with extended physical characteristics.
- Traditional enterprise network configuration techniques, such as VLANs and routing rules are sometimes difficult to implement and manage with limited staff dealing with ICS/OT systems and networks.
- I OT network protocols, in the vast majority of cases, use non-standard messages which are transmitted encapsulated in standard TCP/IP messages. However, the significant (and critical) content for the operation of OT systems remains in the internal non-standard part, specific network devices are therefore needed to analyze these messages in depth (through the DPI).
- Most devices or OT endpoints do not use market standard operating systems making any traditional security strategy complex or impossible.
- La configuration and maintenance of OT systems (SCADA, PLC, DCS, RTU, etc.) normally not is realized by internal staff but from IS outside the company. Situations of external-internal interactions of the corporate network perimeter with obvious security problems are very common.
What does Bayshore Networks offer? Bayshore is the last line of defense!
A suite of Cyber Security devices designed specifically for OT networks that meet the problems indicated above: first of all a real gift from bayshore…SCRUTINY!

Scrutiny is the tool detection and visualization of Bayshore's OT assets: basically allows you to make aAsset Inventory passively, without affecting normal activities.
It allows operators to create a schematic of all the devices on their industrial network, with information regarding the ports and protocols in use to reach or be reached by the different factory devices.
Used periodically, it allows you to find:
- New and/or unexpected resources
- Suspicious network activity
- Dangerous network connectivity
IT'S COMPLETELY FREE, ASK SERVITECNO HOW TO GET IT!
Dinterface device that transfers data from the sensitive network – trusted – (plant) without exposing the machines to an untrusted network – untrusted – (corporate IT, corporate targets) Has the functionality of a one-way data diode that provides an industrial isolation bridge to restrict and enable communications from sensitive and confidential resources
Guaranteed data delivery from source to destination with demonstrable verification, unlike most one-way gateways which use relay methods
It alleviates the cost and complexity of traditional accessand, limited by firewall, or data diodes with a more effective and efficient connectivity solution

OTfuse is an industrial-grade firewall that installs in front of critical endpoints, protecting PLCs and SCADA/DCS devices from unauthorized use, malicious instructions and activities, and remote acquisition from hostile sources. OTfuse features a pair of bypass ports for data in/out, requires no network or resource redirection, and is completely self-contained. No remote management console is required for installation or maintenance.
Evolving security best practices require both application layer and network layer protections. iFIX SCADA has robust application-level features, but is application software that runs on Windows workstations and general IP networks. Therefore iFIX is not itself a network product and cannot mitigate unauthorized network communications. To overcome this problem it is necessary to enhance the iFIX architecture with additional network level security tools. OTfuse iFIX is specifically designed to provide network security for iFIX 6.x installations. It is the only product on the market that provides native deep packet inspection of six proprietary GE iFIX protocols and enables real-time automated protection.
A secure, flexible, OT-specific private remote access solution. It allows for controlled access to resources, designated OT services, and easy user management. OT access is a software-defined remote network access product that can be hosted in the cloud with support for encrypted microtunnels, two-factor authentication, Microsoft Active Directory users and groups, and specific endpoint access capabilities geared towards security requirements and functionality typical of the OT network.
Bayshore is the last line of defense!