Benefits of OT and industrial cybersecurity solutions
Prevent breaches with multiscan
Malware continues to evade defenses as cybercriminals develop increasingly sophisticated threats. OPSWAT ensures security and minimizes supply chain risk by leveraging over 30 anti-malware engines and file vulnerability assessment, preventing the introduction of unsafe files and binaries.
Protection against malicious devices
Removable media and transient devices that contain broken firmware, malware in hidden files/partitions can directly compromise OT endpoints. OPSWAT prevents media and file-based attacks, enforces the use of trusted devices, and verifies that all media and files have been scanned and approved.
Secure multiple delivery paths for content and devices
OPSWAT acts as a secure channel that protects the inbound (ingress) and outbound (egress) delivery paths. Files can be uploaded to the Internet, delivered across network segments, or transported via removable media. Every transferred file and device is scanned to ensure its safety and inspected to avoid the loss of sensitive information.
Uninterrupted access to industrial data
Isolate your networks protected against the propagation of attacks, while providing access to real-time OT/ICS data and enabling secure transfers of IT-OT data and files. OPSWAT one-way and two-way security gateways support a wide range of industrial OT and enterprise IT protocols, with maximum reliability and no data loss.

NetWall transfers data from a secure network (the field) without exposing machines and systems to an exposed network (corporate IT, enterprise network)

NETWALL USG
Supports 50MB, 100MB, 1GB or 10GB, all software selectable to meet your requirements
Support for OPC DA, A&E and UA, plus Modbus/TCP, file transfers and tcp/udp sockets
- Netwall USG transfers data from a secure network (the field) without exposing machines and systems to an exposed network (corporate IT, enterprise network)
- Unidirectional data diode functionality that provides an industrial airgap bridge to limit and enable communications from sensitive and confidential assets
- Guaranteed delivery from source to destination with provable verification, unlike most one-way gateways that use relay methods
- Alleviate the cost and complexity of physical-only access or data diodes with a more effective and efficient connectivity solution
details:
- Physical device located in front of sensitive parts of the network
- Isolated, non-routable, one-way data transfer
- Efficient synchronization and replication of data between systems
- Carries any protocol without proprietary HW and SW vendor
- No network information is exposed as NetWall creates a full protocol break between two network entities
- It supports guaranteed data delivery with better data transmission
NETWALL BSG
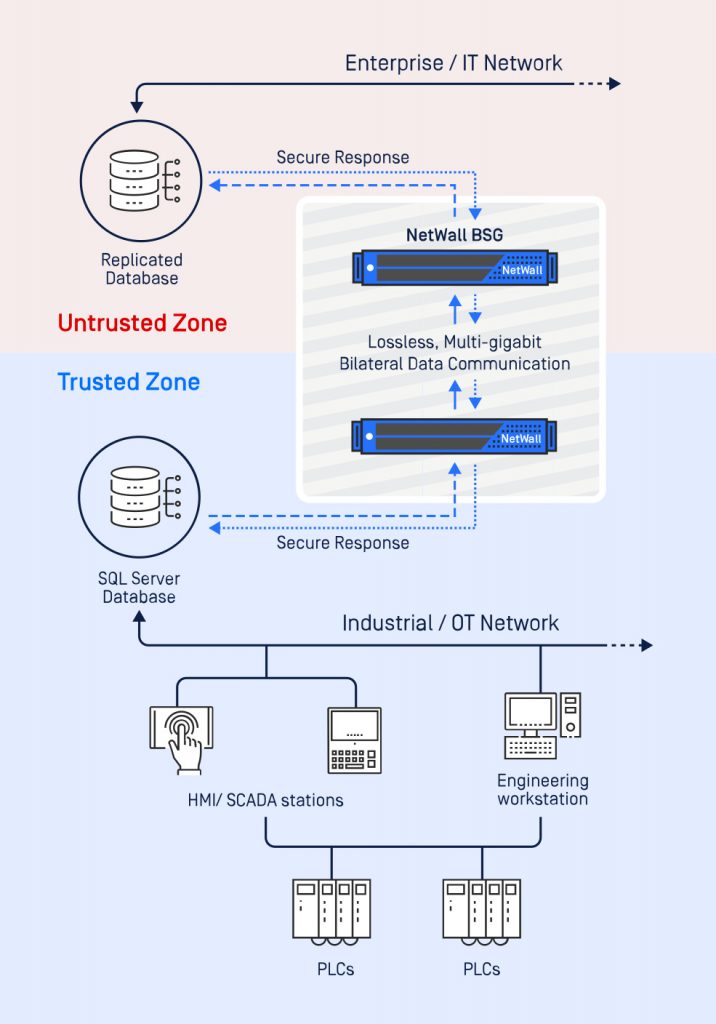
Netwall BSG (Bilateral Security Gateway) incorporates all the features of the NetWall USG (Unidirectional Security Gateway) version, but also adds the ability to receive response data from certain destinations on the untrusted network.
How does it work? Using the NetWall Bilateral Security Gateway solution, a TCP connection is initiated from the protected network to the "untrusted" network. At this point the destination network is authorized to reply to the "sender" by sending data. The permitted activity is only that of reply, while all other autonomous communication activity towards the protected network remains inhibited.
Both NetWall USG and NetWall BSG can securely transfer data from control systems, log files, database records and other data related to IT data centers, Security Operation Centers (SOCs) and based data storage on the cloud.
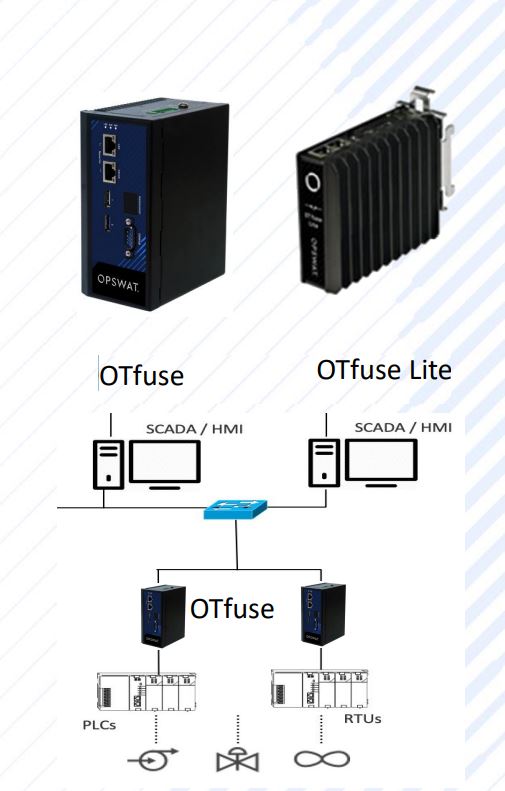 OTfuse it should be placed in close proximity to critical endpoints, protecting PLCs and SCADA/DCS devices from unauthorized use, dangerous instructions and activities, and remote acquisition from hostile sources. It features a pair of bypass ports for incoming and outgoing data packets, requires no network or resource redirection, and is completely self-contained. No remote management console is required for installation or maintenance.
OTfuse it should be placed in close proximity to critical endpoints, protecting PLCs and SCADA/DCS devices from unauthorized use, dangerous instructions and activities, and remote acquisition from hostile sources. It features a pair of bypass ports for incoming and outgoing data packets, requires no network or resource redirection, and is completely self-contained. No remote management console is required for installation or maintenance.
OTfuse is available in variants:
OTfuse offers turnkey protection for PLCs and SCADA/DCS devices
- Native support for modbus, Ethernet / IP, S7, DNP3, BACnet, SLMP, FINS, EGD
- Reports via modbus to the HMIs
- Notices su syslog and email
- Hardware authentication for setup / admin
- Standard container up DIN rail, 24VDC power supply
- Easily installable in <1 hour
Insert. Process. Access.
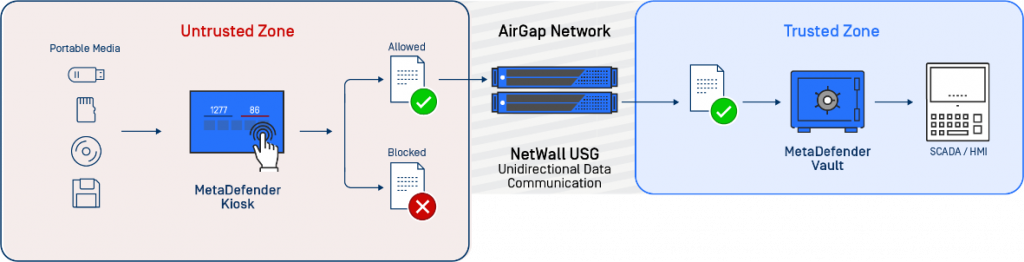
Whenever portable media enters secure environments, critical infrastructure is at risk of being exposed. Software updates, reports and audits require external data sources. MetaDefender Kiosk acts as a digital security guard, inspecting all media for malware, vulnerabilities and sensitive data.
MetaDefender Kiosk acts as a digital security guard, inspecting all media for malware, vulnerabilities and sensitive data.
MetaDefender Kiosk accepts many form factors including CD/DVD, 3,5″ diskettes, flash memory cards, mobile and USB devices, even if encrypted. Once inserted, MetaDefender Kiosk immediately scans for malware, vulnerabilities and sensitive data. Suspicious files can be sanitized. Sensitive files can be deleted.
For users who prefer a Linux operating system, the L Series is perfect. For users who prefer to work with Windows, our K-series kiosks are the right choice.
Product Features
Simplify data transfer
Whether importing files into a secure environment or distributing them as products for delivery, MetaDefender Kiosk establishes a secure process that can be replicated globally.
Industry leading multi-scan
Portable media is a common vector of malware that infects both over-the-air and network-access environments. Combining more than 35 anti-malware engines in one scanning device, the threat detection level can exceed 99%.
Cleaning and rebuilding suspicious files
Deep Content Disarm & Reconstruction (CDR) capabilities actively remove suspicious and unwanted data from common file types, including .doc and .pdf, resulting in clean, usable files.
Data loss prevention
MetaDefender Kiosk provides policy workflows for controlled data file extraction for vendor logs, analytics, etc. Files can be analyzed and reformulated to protect data privacy, sensitive and proprietary information.
Regulatory compliance
OPSWAT supports national and international compliance standards and requirements, including NIST, HIPAA, PCI DSS, GDPR, NERC CIP, NEI 18-08, ISA/IEC, and ISO/IEC.
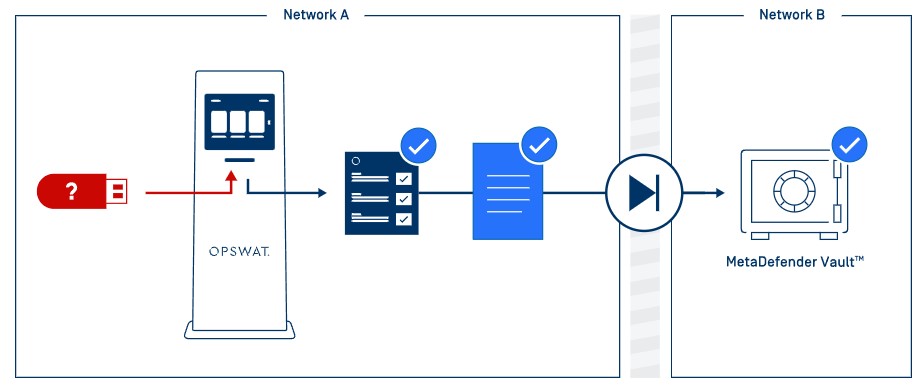
Ensure security and trust across the perimeter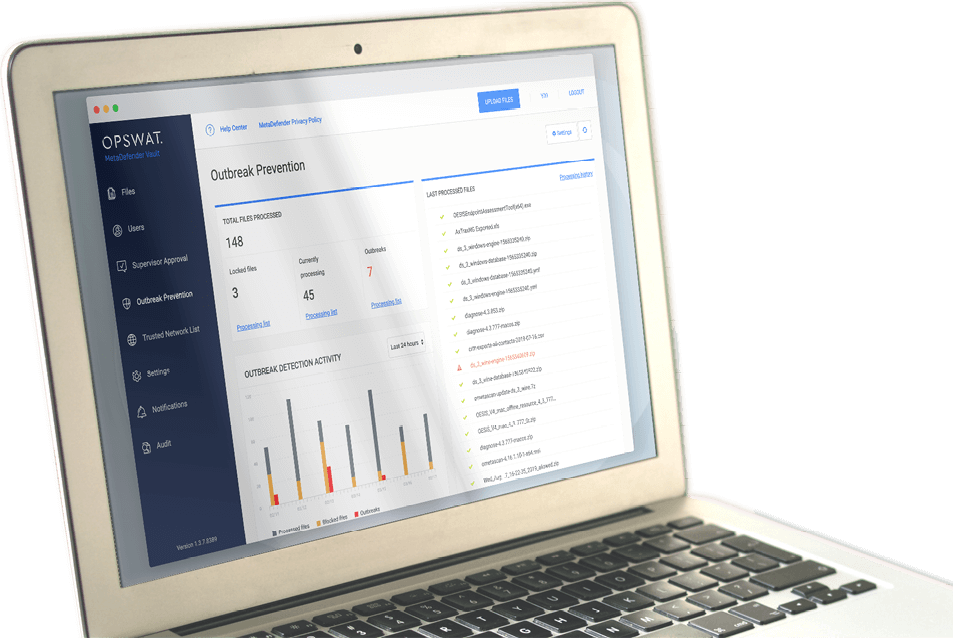
Transferring files into and out of any network environment exposes systems in that environment to breaches and infections. Portable and removable media are often used to make these transfers, bypassing security protocols.
MetaDefender Vault is a secure file storage and retrieval solution that protects critical data and keeps threats away. Provides a multi-level approval process and detailed audit trail for data transfers within an organization.
secure. He approves. Access.
- As files enter MetaDefender Vault, they are scanned for malware and vulnerabilities by over 35 of the computer industry's best malware and heuristic engines.
- Files are continuously rescanned and evaluated as virus definitions are updated to avoid zero day incidents.
- Suspicious files are sanitized.
- Rules can be created to block access to files for a pre-specified containment period to allow for vendor scans and engine updates for new zero day outbreaks.
- Approval sequences and workflow functions confirm who should authorize incoming and outgoing files and who can access them.
Assess threats on any USB bootable system
Transient devices such as laptops can be compromised when used outside of secure facilities and networks. These are laptops of contractors, traveling executives, remote access workers, etc. Other vectors of compromise for transient systems include the infiltration of private or controlled proprietary data.

In addition to transient devices, development environments and related software development environments can be compromised through shared open-source code. Software development entities that supply hardware systems alongside developed software may actually be supplying compromised systems to their internal or external customers.
MetaDefender Drive it's the protection these systems need. It is a secure USB bootable firmware used to evaluate malware, vulnerabilities and sensitive data in any USB bootable system. MetaDefender Drive uses intrinsic system resources (CPU and RAM) to process boot partitions and all files on internal drives. It has also been optimized to reduce footprint for resource constrained devices often found in critical infrastructure, such as laptops with 1G RAM and 1 CPU.
All companies that have transient resources or send pre-installed systems to internal or external customers need the protection of MetaDefender Drive. Anyone using a single vendor's antimalware and heuristics engine is putting their business at risk. MetaDefender Drive comes with up to five separate vendor engines for analyzing and identifying malware, vulnerabilities, countries of origin, and data loss protection.
Insert. Reboot. inspect
- Scan the device, including the boot sector
- Multiple scan engines, including McAfee, AVIRA, Bitdefender and more. Detect threats that others may not notice.
- Compromised systems forensics allows you to copy valid files to a secondary storage device or to the MetaDefender Vault.
- Scan for tens of thousands of known vulnerabilities.
- Support of online and offline environments (internet optional).
- Detect sensitive data in stored documents, images and videos.
- Detects software components produced by foreign adversaries.
- It supports all popular operating systems: Windows, Linux, macOS.
- It supports hard drives encrypted with BitLocker, FileVault, LUKS and more.
- Analysis, reporting and implementations are managed centrally through OPSWAT Central Management.
Another option to secure and control the use of portable media in critical infrastructure

The firewall USB MetaDefender of OPSWAT offers another option to safely and securely leverage the productivity, flexibility and convenience benefits of portable media in IT or OT SCADA environments.
Complementing MetaDefender Kiosk, MetaDefender Vault and OPSWAT client for Windows, Linux and Mac, MetaDefender USB Firewall offers a plug-and-play, no installation and no software clutter path to portable media protection, ensuring that the industry boot files and portable media file contents are inspected, verified, sanitized, and approved prior to use.
Benefits
- Automatic blocking of raw or compromised files
- Portable media security helps you comply with policies, regulations, and standards, including NERC CIP, ISA 62443, NIST 800-53, NIST 800-82, and ISO 27001.
- No software installation required; perfect for locked down HMI SCADA application environments
- Boot sector protection
- Works with MetaDefender Kiosk Manifest to verify files
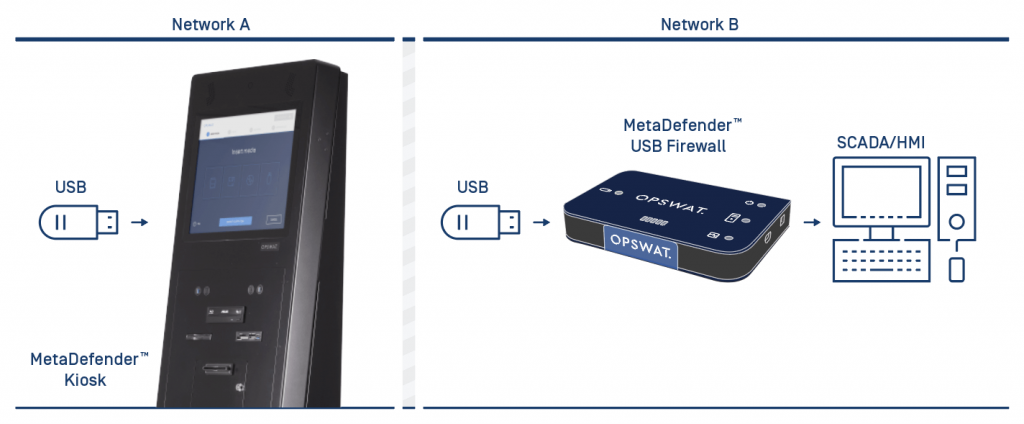
Advanced Threat Prevention for Endpoints
OPSWAT Client protects endpoints within critical networks from at-risk removable media. Files can be scanned and sanitized using OPSWAT's industry-leading threat prevention technology, such as multiscanning and Deep Content Disarm and Reconstruction (CDR).
The use of removable media can be regulated and audited based on the security and compliance requirements of organizations.
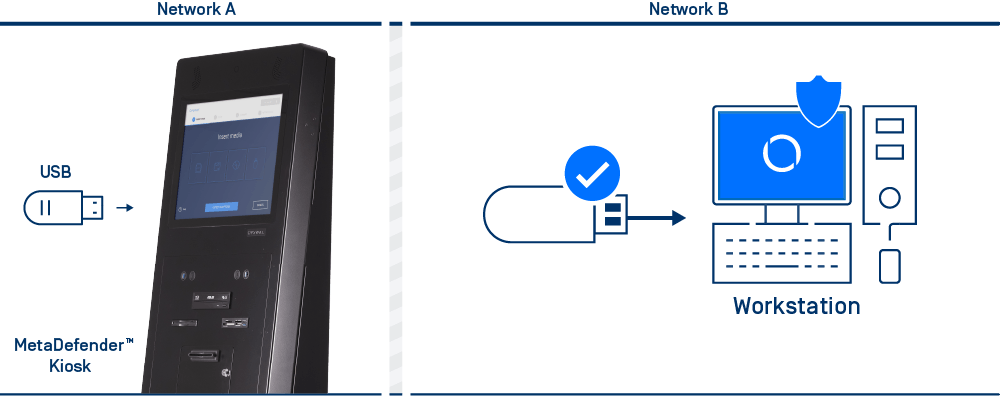
Features
Protection of removable media
Block access to USB drives and other removable media devices until security conditions are met.
Multiscan and Deep CDR
Provides a second layer of defense against threats by scanning your system with multiple anti-malware engines and performing a Deep CDR on over 100 file types.
Forced use of media
The use of removable media can be allowed only if certified by MetaDefender Kiosk.
Inspection of archives
Examine files contained in archives, both encrypted and unencrypted. Encrypted devices are also supported.
Online and offline support
It supports online and offline working environments. When used with MetaDefender Kiosk, it can support a secure workflow for transferring files over networks with air coverage.
Support for cross-platform operating systems
Windows 7, 8, 8.1, 10, Windows Server 2008 R2, 2012, 2012 R2, 2016 and Debian, Ubuntu and CentOS Linux.
Advanced threat prevention and device security management platform
Central Management allows you to monitor and manage multiple MetaDefender products from a single location. From a centralized console, you can perform global operations such as view managed antimalware engines, manage virus definitions and engine updates, and check license status.
Features and benefits
Inventory at a glance
The entire fleet of MetaDefender instances and SafeConnect NAC at a glance on one page.
Management at scale
Group MetaDefender instances by type, geographic location or business unit. Apply flexible policies, settings and workflows to different groups.
MetaDefender Dashboards
Aggregate events worldwide. View file processing history by instance, group or globally with a customizable time window. See real-time events and threat statistics for your critical infrastructure. Analyze threat trends over time.
Centralized upgrade of the AV engine
For online environments, all antivirus engine updates and definitions are downloaded directly from OPSWAT's update servers and applied automatically. For offline environments, updates can be downloaded using OPSWAT's Update Downloader utility and then transferred to Central Management for automatic distribution between different MetaDefender API installations.
Endpoint security policy compliance
Flexible policies for different groups of devices. Non-intrusive on-demand agent for BYOD devices, helping you ensure security compliance for your work-from-home employees.
A one-way security gateway is a cybersecurity hardware solution that ensures the one-way transfer of information between two networks. Traditionally based on a fiber optic connection to ensure one-way data transfer, the data diodes can encounter transmission reliability and data overrun issues, while modern one-way security gateways include assured delivery mechanisms to overcome these challenges. One-way gateways and data diodes have been commonplace for decades in high-security environments, such as defense and intelligence agency facilities.
With the rise of industrial IoT and digitalization, one-way security gateways are increasingly used by private companies to securely transmit data generated by industrial control and security systems.
This includes nuclear power plants and other electrical power generation facilities, manufacturing facilities, and transport systems to other networks (including the public Internet), while gateways protect the networks containing these systems from attack.
Unidirectional means that data can only travel in one direction. A reasonable way to think of one-way security gateways is as “data one-way valves,” which allow data out, with no way back. A common scenario is where one-way gateways provide one-way data transfers from a high-security network to a lower-security network. Data can be transferred while the high security network remains protected from attacks over this connection. In this scenario, the diode protects the high security network systems that produce the transferred data.
Scan. Sanitize. Keep.
Enterprise storage providers such as Dell, Amazon (AWS), Microsoft (Azure, OneDrive, SharePoint Online, Teams), Google (GCP, Google Drive), Box and Dropbox have embraced digital transformation and provide both cloud-based and online services. - he premised. These hybrid solutions are adopted globally, but have led to an increased attack surface that puts organizations at risk.
Sensitive and confidential private information can be accidentally stolen or shared, leading to potential compliance violations and fines.
Employees may accidentally share personally identifiable information (PII) documents or sensitive content with unauthorized recipients, thereby violating privacy laws and regulatory requirements such as HIPAA, PCI-DSS, FINRA, and the GDP. This can result in significant fines and penalties and incalculable loss of reputation.
Benefits
Useful Information
Instant view of the health of all enterprise data storage instances. A clear and concise dashboard highlights the threats and vulnerabilities affecting your data.
All cloud and on-premise storage solutions in one place
Gain visibility into one comprehensive view to monitor and protect the health of all your enterprise data, both in the Cloud and On-Premises, through native API integrations with storage and collaboration solution providers.
Simple installation
Use our lightweight installer and import your own configurations or configure them from scratch. All of this in an easy-to-use interface that guides you step-by-step through onboarding and has you ready to go in minutes.
Processing options and history
Choose a combination of real-time processing and scheduling options to keep your archive safe from zero-day attacks and advanced persistent threats.
Remedial actions
Besides file processing (with multi-AV scans, data sanitization, vulnerability assessment), users can configure appropriate remediation actions for different outcomes.
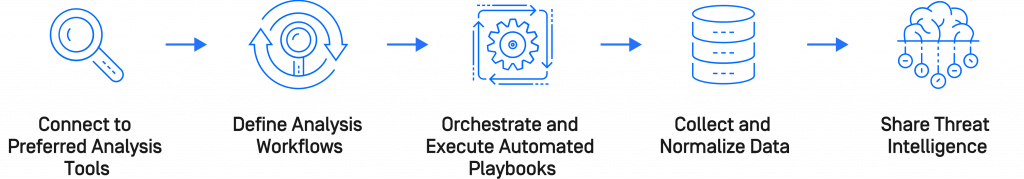
Smarter malware analysis for critical infrastructure

One stop solution for your malware analysis needs
- Integrate all required analytics components from a single console
- Easy-to-use framework for analytics orchestration, automation, and reporting.
- Tackle file-based threats in critical IT and OT infrastructure.
Full automation across multiple tools – for both OT and IT-based threats
- The automated playbooks include OPSWAT's analytics technologies and popular third-party tools.
- Improve incident response with timely and actionable intelligence consolidated across tools
- It offers increased performance and scalability to ensure no threat goes uninvestigated
Quick threat intelligence
Advanced threat prevention for network traffic
Cybercriminals are relentlessly trying to load malware onto your systems. Employees accidentally visit malicious websites or download malicious files and vulnerable software from the Internet. Internal and external users send, intentionally or unintentionally, files containing sensitive data.
Businesses need a powerful layered cybersecurity system to prevent harmful, offensive or inappropriate content.
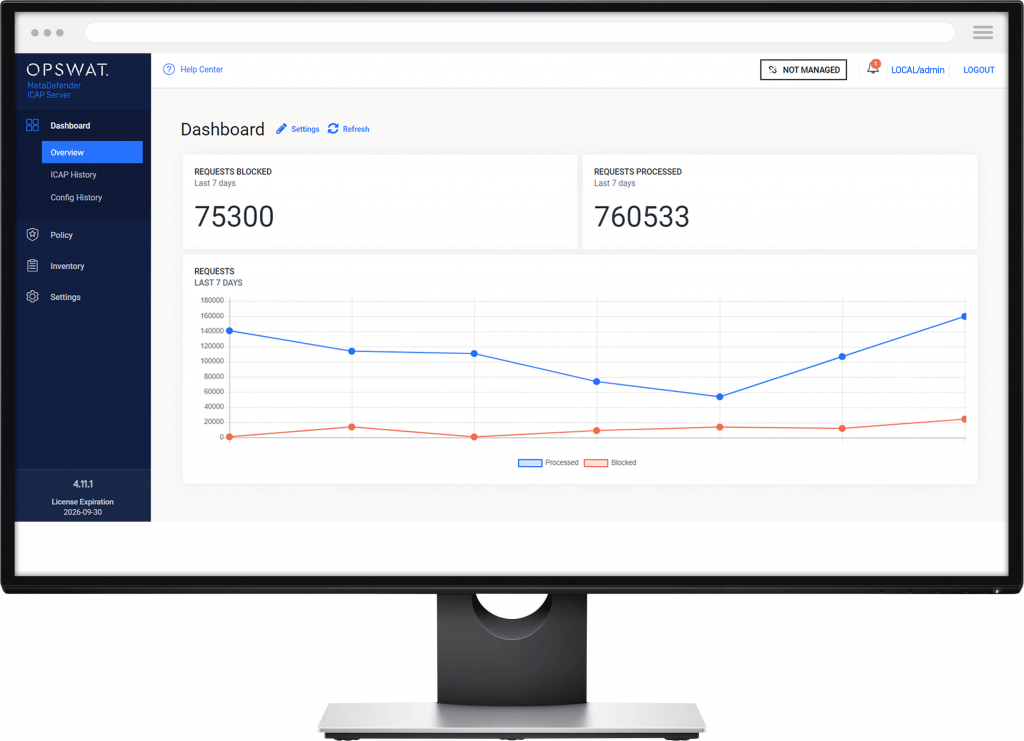
MetaDefender ICAP Server protects systems and users by inspecting every file that traverses the network. Each file is scanned for malware and vulnerabilities. Thanks to customized policies and workflows, suspicious files can be blocked or deeply sanitized. Sensitive information is locked down, removed or scaled down before leaving the network. All files are patched before being accessible to the end user.
MetaDefender ICAP Server is a plug-and-play solution for protecting your network from harmful Internet content.
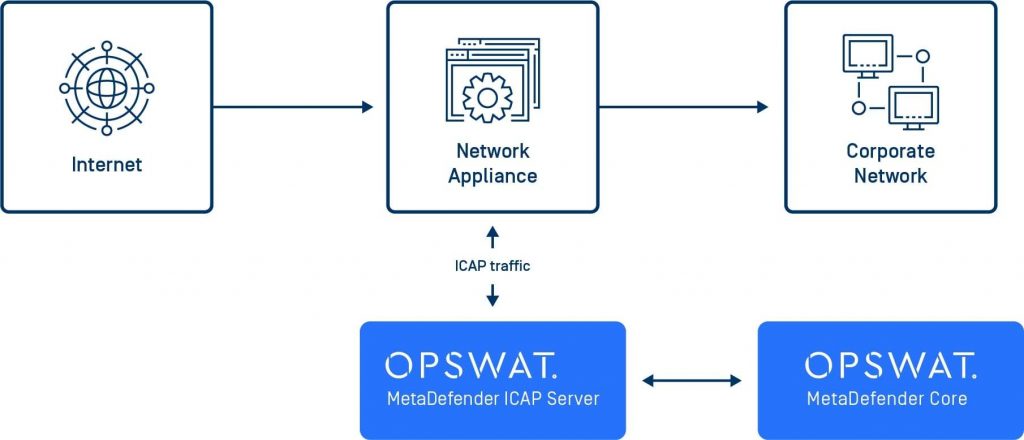
How an ICAP server works
MetaDefender ICAP Server provides an ICAP interface on top of MetaDefender Core to provide industry leading advanced threat protection. Any content routed through the ICAP interface is scanned and processed before entering the network and reaching end users.
MetaDefender ICAP Server can seamlessly integrate with any ICAP-enabled network device, including reverse proxies, web application firewalls, load balancers, forward proxies, web gateways, SSL inspectors, etc.